Ubuntu, a widely adopted Linux distribution, is a staple in various environments, from servers and desktops to cloud platforms. A key system administration task is managing user accounts.
For anyone running an Ubuntu system, whether it’s a dedicated server, a Virtual Private Server (VPS), or a cloud-based instance, understanding how to retrieve a list of users is crucial. Even in shared hosting scenarios, where environments are often shared, knowing the users is vital for security and management.
This guide provides different methods for listing users on your Ubuntu system.
Let’s begin!
Step 1: Using the `cat` Command
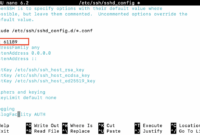
The most direct method to list users involves displaying the content of the `/etc/passwd` file. This file stores user account information.
cat /etc/passwd
The output will display each user on a separate line, along with details like username, user ID (UID), group ID (GID), home directory, and default shell.
Step 2: Using the `awk` Command
If you only need a list of usernames, you can use the `awk` command to extract that specific information:
awk -F: '{ print $1 }' /etc/passwd
This command processes the `/etc/passwd` file, using the colon (`:`) as a delimiter, and prints only the first field, which represents the username.
Step 3: Using the `getent` Command
The `getent` command retrieves entries from various system databases. To get a list of users, use the following:
getent passwd
This method is especially useful when your system uses the Name Service Switch (NSS) and user information might be sourced from locations other than the local files, such as Lightweight Directory Access Protocol (LDAP).
Step 4: Using the `compgen` Command
The `compgen` command, primarily designed for command completion, can also be used to list users:
compgen -u
Commands Mentioned
- `cat /etc/passwd` – Displays the content of the `passwd` file, showing all users and related information.
- `awk -F: ‘{ print $1 }’ /etc/passwd` – Extracts and displays only the usernames from the `passwd` file.
- `getent passwd` – Retrieves user entries from system databases.
- `compgen -u` – Uses command completion to list usernames.
FAQ
-
Why is it important to list users in Ubuntu?
Listing users is essential for various system administration tasks, including user account management, security auditing, and ensuring correct access permissions. Knowing who has access to a system is a key component of security maintenance and ensuring system integrity.
-
What is the difference between `cat` and `awk` in listing users?
Both commands can list users, but `cat` displays the entire contents of the `/etc/passwd` file, providing all user details. In contrast, `awk` allows you to filter and display specific fields, such as just the usernames, making the output cleaner and more focused.
-
Can I use these methods on other Linux distributions?
Yes, these methods are generally applicable to most Linux distributions, not just Ubuntu, as they rely on standard Linux utilities and core system files.
-
How can I list only specific users or groups?
You can combine `grep` with other commands to filter the output and list specific users or groups. For example, `cat /etc/passwd | grep ‘username’` will display only the details for the specified username.
-
Is there a GUI method to list users in Ubuntu?
Yes, Ubuntu offers a graphical user interface tool called “Users and Groups” that allows for user management, including listing users. You can usually find it in the system settings or control panel.
Conclusion
Listing users in Ubuntu is a fundamental skill for any system administrator. Regardless of whether you’re managing a large server infrastructure or a personal desktop, knowing the users on your system is essential for ensuring security and performing management tasks.
This guide has provided a variety of commands and techniques that allow you to easily list users.
Remember that whether you’re working on a dedicated server, VPS, cloud platform, or even a shared hosting environment, understanding your user base is crucial for achieving optimal system performance and maintaining robust security.
Your comments are welcome below.